This week, we’ll cowl a brand new malware specimen referred to as Sysjoker and a information for Linux reminiscence forensics. Though the forensics information isn’t complete and definitely not in full element, it’d assist in understanding the fundamentals of a reminiscence extraction and evaluation course of utilizing Volatility.
Sysjoker Backdoor
In a latest submit by Intezer, the authors analyzed a brand new backdoor able to working on a number of working programs. In line with the evaluation, “Sysjoker” can run on macOS, Linux, and Home windows.Sysjoker hides as a system replace and makes use of completely different strategies to cover and alter its Command and Management (C2) server’s IP handle.
It’s additionally regarding that the pattern got here clear from VirusTotal scans, which can point out that the backdoor is pretty new. Though the strategies it makes use of to contaminate a system are completely different on varied working programs, as soon as it beneficial properties persistence on a system, it begins speaking with the C2 server. Within the evaluation, Intezer states that they haven’t seen a subsequent stage instruction from the C2 server but. The submit suggests utilizing reminiscence scanners to detect the malware.
One other manner of doing forensic evaluation is to dump the reminiscence and analyze it with a widely known device like Volatility. Within the older variations of the Linux kernel, dumping the reminiscence might be achieved by copying the digital reminiscence from /dev/mem utilizing a command-line device like dd; nonetheless, this technique was deprecated due to potential safety implications.
Linux Reminiscence Forensics
We are able to sum up forensic evaluation because the completely different strategies utilized in proof acquisition, evaluation of proof, and documentation of the implications of a safety incident. After a confirmed safety breach, a forensic evaluation normally takes place to grasp higher what went on in a compromised system. There are quite a few sources of proof that you could analyze to make defensible claims in regards to the supply of an incident; nonetheless, we’ll solely do a hands-on reminiscence evaluation of a compromised Linux system to reveal a few of the methodologies and instruments you need to use.
Reminiscence
RAM, by nature, is unstable. It requires fixed energy to undergo it to operate, and it will get reset each time a system reboots. Linux retains the info saved in reminiscence beneath the /dev/mem listing; nonetheless, it’s not possible to extract artifacts from reminiscence utilizing this partition immediately in newer distributions. It’s because beginning in Linux kernel 4.16, an choice (CONFIG_STRICT_DEVMEM) will get enabled by default to disallow entry to this delicate partition.
Though this makes it tougher to amass the reminiscence picture, it additionally makes it harder for adversaries (and inexperienced customers) to trigger devastating harm to the system. An attacker with root entry to the system might use the mem gadget to inject code immediately into the kernel if this selection is disabled.
We’ve spun up a Debian 9 Linode with the hostname “forensics” in one among our knowledge facilities for this demonstration. We configured the forensics field to be an instance of a constructing and evaluation atmosphere. Though it’s not essential to do these on an exterior machine, tampering with a pc that holds proof is inadvisable. Listed below are the steps to our evaluation:
- Create a Volatility profile for a compromised system utilizing a machine with the identical OS and kernel construct/model.
- Dump the reminiscence along with your device of selection (AVML on this demo).
- Examine the dumped reminiscence utilizing the profile you’ve created for Volatility with the assistance of plugins.
Warning
We are going to use the Python 2 repository of Volatility for demonstration functions due to the compatibility points presently in progress with Volatility 3. We’re conscious that assist for Python 2 resulted in 2020; that is strictly to reveal using the device in a managed atmosphere. In the event you’d prefer to observe together with the information, please accomplish that at your personal threat.
Necessities
By default, Debian 9 Linodes will lack a few of the instruments we’re going to make use of on this demo. It’s advisable to put in all of them with the next command earlier than continuing with different directions:
sudo apt set up make git zip dwarfdump linux-headers-$(uname -r) python-pip python-distorm3 python-cryptoVolatility
The Volatility Framework is a totally open assortment of instruments carried out in Python beneath the GNU Normal Public License to extract digital artifacts from unstable reminiscence (RAM) samples.
It’s vital to make sure that the right Volatility profile will get used when analyzing a reminiscence dump. A profile is a file containing details about a kernel’s knowledge construction and debug symbols that can be utilized to parse a reminiscence picture correctly. Fortunately making a profile with Volatility is sort of easy. You may as well take a look at the repository of Volatility profiles for some pre-built profiles.
Constructing A Profile
After putting in the mandatory instruments, we will start constructing our Volatility profile for the machine it’s working on.
1. git clone https://github.com/volatilityfoundation/volatility ~/volatility
2. cd ~/volatility/instruments/linux/
3. make
4. zip ~/$(lsb_release -i -s)_$(uname -r).zip ./module.dwarf /boot/System.map-$(uname -r)
5. cp ~/$(lsb_release -i -s)_$(uname -r).zip ~/volatility/volatility/plugins/overlays/linux/
6. python ~/volatility/vol.py --info
The preliminary line (1) will clone the Volatility repository into the consumer’s residence listing. By going into the (2) ~/volatility/instruments/linux listing, we will use make (3) to recompile the modules of the kernel. It’s vital to have the kernel headers downloaded beforehand, in any other case this course of would possibly fail.
This leads to a module.dwarf. Then the following command (4) makes use of this module to learn the system map from /boot to generate the profile we have to use in Volatility. We are able to then copy this profile (5) over to the proper listing, in order that Volatility can use it. Lastly, to confirm our profile is correctly loaded into Volatility we will run Volatility as soon as with the information flag (6). If all of the steps are profitable, we must always see our customized profile within the Profiles part of the output.
Putting in a Hidden Kernel Module
For this instance we’ve used HiddenWall to generate a hidden Linux Kernel Module (LKM), named it ‘cantfindme’, and loaded it onto one other Debian 9 Linode with the identical kernel construct/model because the ‘forensics’ machine. Though the module is loaded, it might’t be seen when lsmod or modprobe is executed on the system:

Reminiscence Acquisition
There are nice instruments that you need to use to dump the reminiscence in Linux; nonetheless, on this information, we’ll go along with AVML (Purchase Unstable Reminiscence for Linux) since LiME is roofed often on the internet. AVML is an open-source reminiscence acquisition device for Linux made by Microsoft. Yow will discover the newest launch right here and obtain the binary to the machine from which you need to dump the reminiscence. Do not forget that the pc we’re dumping the reminiscence from should have the identical kernel/OS construct and model because the Volatility profile we’ve generated beforehand.
In a real-life situation, it’s vital to not tamper with a compromised system to make sure the proof we accumulate could also be admissible in a courtroom of legislation. It’s additionally vital to not compress any photographs every time doable as a result of bit-by-bit acquisition might present knowledge {that a} compressed picture might not.
After downloading the AVML binary onto the house listing, you need to use the next command to dump a system’s reminiscence to the house listing.
sudo ~/avml ~/output.limeAVML will dump the reminiscence in LiME format, in order that we will start our evaluation with the Volatility profile we’ve created. You may as well take a look at the scale of the dump to make sure it matches the full RAM on the gadget. Volatility shouldn’t tamper with the reminiscence dump, nevertheless it’s higher to make a replica of the file and to investigate the copied knowledge as a substitute of the unique after guaranteeing that their hashes match.
After dumping the reminiscence of the ‘pwnd’ field, we’ve transferred it to the ‘forensics’ field for evaluation.
Volatility Plugins
Volatility affords quite a few plugins to help the forensic analyst. Yow will discover an inventory of those plugins of their Github web page. By utilizing Volatility plugins we will get a fast overview of the reminiscence picture. The command format for analyzing a reminiscence picture could be discovered beneath:
python ~/volatility/vol.py -f <path_to_memory_dump> --profile=<profile>
<plugin_name> <plugin_options>Right here’s the output from the plugin linux_hidden_modules that lists the hidden loaded kernel modules from the reminiscence picture:
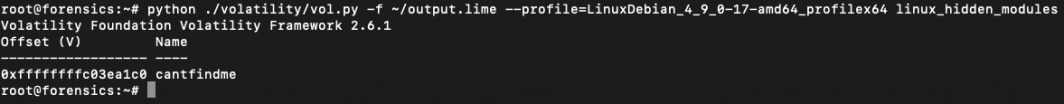
This plugin will help you discover hidden Linux Kernel Modules that could be malicious. Even when these modules can’t be seen once you run lsmod on the system, they’ll each be detected and extracted from a reminiscence dump. You need to use the linux_moddump plugin to dump the kernel modules both by specifying their identify in a regex sample or by specifying the bottom handle of the module within the reminiscence picture:
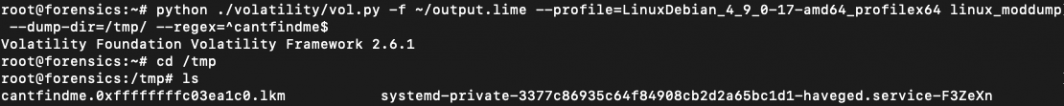
There may be extra that may be finished with Volatility that we merely can’t cowl on this submit. Be at liberty to depart a remark down beneath to share your ideas and options.