
As extra individuals undertake digital platforms to deal with communications, safety turns into an more and more vital concern. This isn’t an sudden growth. By most metrics, there are greater than 4 billion lively web and digital communication customers as of 2021. It’s an accumulation that’s over 20 years within the making.
For a lot of, nevertheless, digital communication platforms are nonetheless a novelty. Many of those new and long-term customers have considerations concerning the security of utilizing these infrastructures, both pretty or unfairly. With somewhat investigation, it’s clear sufficient that service suppliers are very severe about digital communication and web site safety, however what measures are taken?
The chances are high that, at one time or one other, you’ll have heard one thing about end-to-end encryption (E2EE). This is a crucial safety function for a lot of digital communication companies. Extra to the purpose, it’s one thing that each person ought to have at the very least some primary data about.
This newbie information will train you what E2EE is, the way it works, and why it’s so vital. Think about this your end-to-end encryption pocketbook.
What’s Finish-to-Finish Encryption?
One of the well-known types of encryption, end-to-end encryption has been adopted by an enormous quantity of companies and platforms over the previous couple of many years. For the reason that wider public is now utilizing software program that depends on E2EE, there’s a better want for understanding than there’s ever been beforehand.
It isn’t too sophisticated, actually.
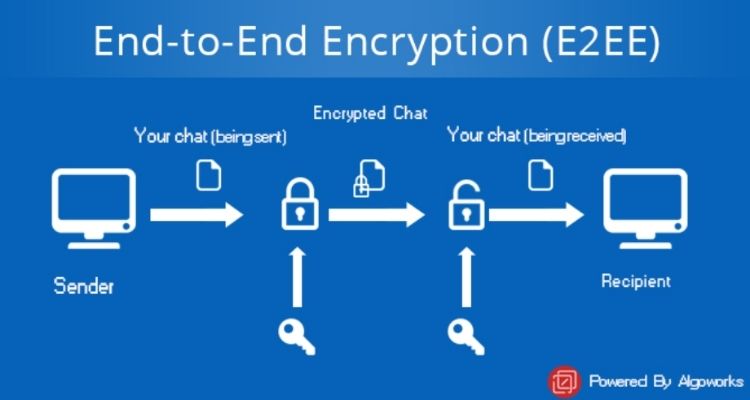
Finish-to-end encryption is a extremely safe technique of communication. With E2EE, any information is encrypted earlier than the machine sends out the message. Whereas en-route to its receiver, the information is unreadable by those that would possibly search to take a peek. Solely as soon as it reaches the receiver is it attainable for the decryption to happen – and solely then by the receiver.
Understanding the Fundamentals of Encryption
Finish-to-end encryption is without doubt one of the extra outstanding types of encryption in the intervening time. And that’s precisely it – it’s simply one among many alternative encryption varieties.
Accordingly, it’s vital to begin with the fundamentals – like what precisely encryption means.
Talking merely, encryption is a technique for muddling information (encrypting) in order that it isn’t readable by simply anyone. With a view to see the information, it’s essential have the power to unscramble (decrypt) it.
We stay in a world the place privateness is an more and more uncommon commodity. This has seen encryption expertise a substantial elevation in worth.
Most individuals work together with encryption techniques regularly. They usually do that unknowingly. From social media apps and display sharing software program to e mail companies and banking web sites, a lot of what you employ has some type of encryption.
Finish-to-end encryption is a particular technique for scrambling and unscrambling information – so, how does it work?
How Does Finish-to-Finish Encryption Work?
For rookies, encryption applied sciences appear nearly magical. However these techniques work off well-established rules which have skilled strong testing over time.
For true E2EE, scrambling happens on the machine degree. What this implies is that any messages despatched from a tool are encrypted earlier than they depart. Clearly, they’re decrypted as soon as they’re obtained by the meant person. Since most digital communication platforms depend on messages passing by interchanges, this encryption is important.
The system relies on the creation of a public-private cryptographic key pair. Generally generally known as uneven cryptography, this course of makes use of separate keys for encrypting and decrypting the information. Public keys work by scrambling the information and the keys broadly distributed. However, non-public keys are used to unlock the message. Crucially, solely the proprietor is aware of the non-public key.
For every person who’s concerned within the communication, E2EE techniques create and distribute private and non-private keys.
The place Is Finish-to-Finish Encryption Used?

Now you know the way end-to-end encryption works, however the place would possibly or not it’s used?
Most individuals are in all probability conversant in E2EE on account of companies like WhatsApp, however these cybersecurity measures are current in all places.
Listed here are just a few software program classes the place end-to-end encryption is a should.
1. Video Conferencing Software program
You’re in all probability already conscious that video conferencing platforms have exploded in reputation lately. There are numerous the reason why companies would possibly combine these applied sciences.
It’s clear, although, {that a} video conferencing resolution for small enterprise and huge enterprise operations should embody end-to-end encryption. Given the delicate nature of the data that passes by these channels, they merely can’t do with out it.
2. E mail
Now, right here’s a expertise that feels as previous as time itself. In each non-public {and professional} conditions, it’s quite common to trade delicate data over e mail.
There’s a purpose that e mail is without doubt one of the hotspots for hacking makes an attempt – there’s a treasure trove of information to mine. Fortunately, the vast majority of e mail suppliers provide strong end-to-end encryption to safeguard this information.
3. Chatbots
A relative newcomer on this area, chatbots have modified the best way that buyers work together with companies.
Chatbots use robotic course of automation (RPA) expertise to obtain requests and execute the mandatory duties. For many who are unfamiliar, a fast RPA definition tells us that it’s a type of expertise used to copy human actions for digital duties.
These chatbots will obtain important, delicate data from the person. To securely full the required duties, end-to-end encryption is important.
4. Messaging Apps and Companies
Messaging apps and platforms are used as a lot, and maybe extra, than e mail for many individuals.
They’re weak in the identical method that your e mail accounts might be with out end-to-end encryption. WhatsApp, Viber, and iMessage are just a few examples of messaging companies that use E2EE.
Why Is Finish-to-Finish Encryption Essential?
Many individuals don’t take care of advanced expertise on a frequent foundation, and except you’re employed in cybersecurity or interact in crypto initiatives, it may be arduous to grasp why encryption is vital. Nonetheless, these techniques matter an important deal.
What Does E2EE Defend You From?
Digital safety won’t be one thing you consider usually, or in any respect, but it surely has a direct influence on you on daily basis.
Primarily, E2EE is used to stop individuals from viewing your messages and information. Since solely the end-users are capable of see the message, unhealthy actors gained’t have an opportunity to intercept your communications.
Take this instance.
A enterprise makes use of an interactive voice response (IVR) system to collect data from their clients earlier than directing them to the workforce they want. The knowledge gathered might be delicate – assume social safety numbers, as an example – and that raises safety considerations.
If the IVR system doesn’t make use of end-to-end encryption, this information is weak. A leak of this nature might show catastrophic for an individual. However, when the information is encrypted, these considerations crumble.
However end-to-end encryption isn’t simply nice at preserving individuals from viewing your information. It additionally works wonders at defending the information from tampering. On account of E2EE, the information isn’t legible. Consequently, there’s no technique that might reliably alter the information – and any such try can be blatant. Once more, this holds substantial significance.
Let’s take a look at one other instance.
On this situation, a advertising and marketing division is planning on utilizing analytics software program to create a brand new data-driven technique for the enterprise. They’ll collect information simply sufficient, in order that’s not a priority. But, they fail to consider the correct safety measures wanted to rebuff any tampering makes an attempt.
On this state of affairs, they may obtain misguided information – information that misdirects their technique. Utilizing encryption techniques would have eradicated this downside on the supply.
Business Advantages of Utilizing Finish-to-Finish Encryption
You’ll be able to in all probability inform from the above examples that encryption is particularly vital for companies. Why is that?
1. Constructing Belief and Confidence
In the event you’re offering a communication platform for personal customers and different companies, they should know that their data goes to be safe.
Area and web site internet hosting companies are good examples of companies that might undergo from errors.
A few of these companies provides ai area identify registration companies, permitting companies to affiliate themselves with synthetic intelligence. Extremely futuristic. If, nevertheless, they fail to indicate that their internet hosting companies are safe, individuals will take their enterprise elsewhere – regardless of the pull of such domains.
When companies show that they’re severe about encryption and safety, it breeds confidence within the firm. For industrial customers, specifically, this may be the distinction between adopting a service and shifting onto one thing else.
2. Avoiding Lack of Capital
You’ve in all probability heard within the information of information breaches going down. But, it won’t have occurred to you that these breaches may end up in vital monetary hardship.
Theft is an actual concern, however lacklustre encryption and safety measures might additionally land you in scorching water with regulatory organizations just like the FTC (Federal Commerce Fee).
3. Guarding Delicate Information
The very objective of end-to-end encryption is to guard information. What you won’t have realized but is simply how impactful leaked information might be.
For the typical US citizen, having their messages leaked would result in embarrassment. For a enterprise, the results are doubtlessly extra severe. You might lose a market edge, upset your employees as their particulars are leaked, or launch product specs.
Unscrambled: The Significance of Finish-to-Finish Encryption
Digital communication is sensible, accessible, even pleasant. However for a safe expertise that gained’t hurt you in the long term, end-to-end encryption is important.
As consciousness of digital safety dangers grows, so does the thirst for extra data. Folks need to guard their private and industrial information like by no means earlier than. These days, they should know that the platforms they’re utilizing are serving to them do precisely that.
Don’t make the error of scrimping on safety measures – they’re basically vital.
Learn extra: