ASP.NET MVC is an online software framework developed by Microsoft that works on the mannequin–view–controller (MVC) sample.
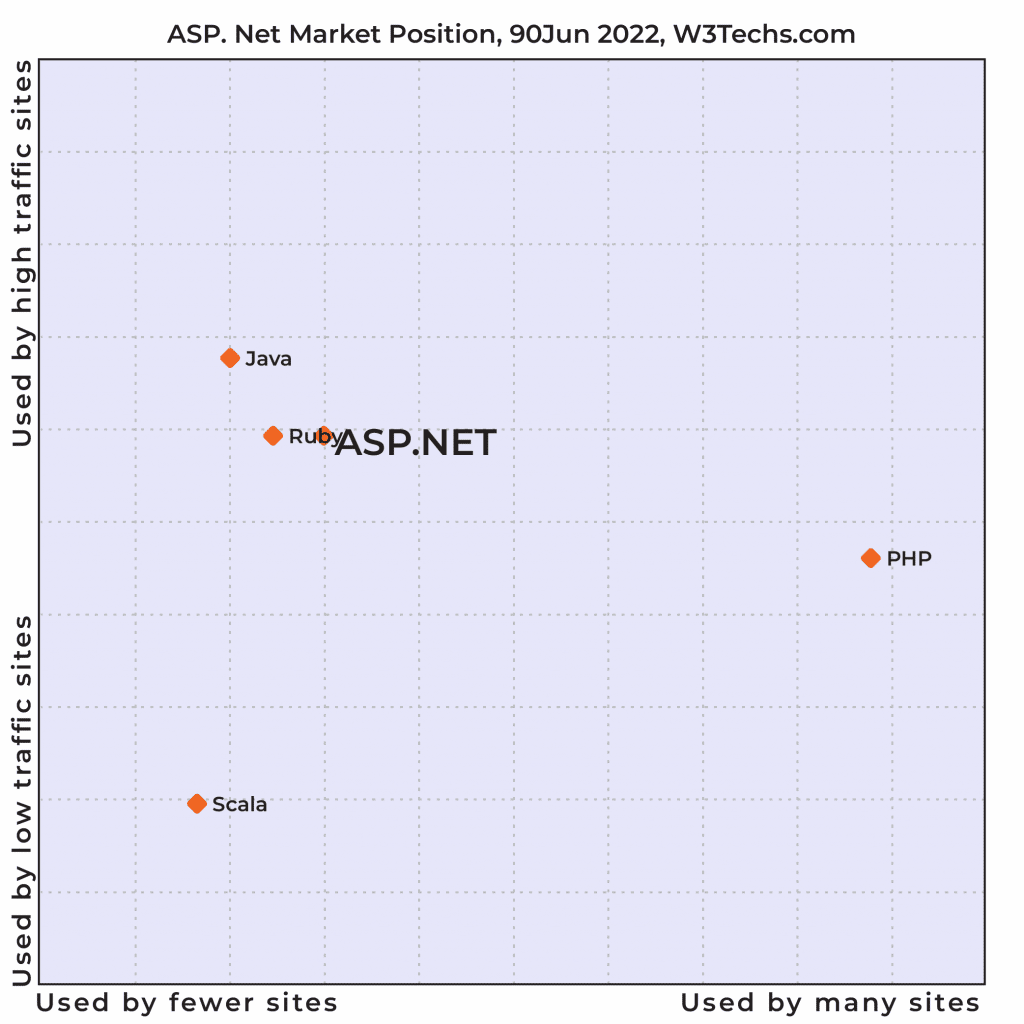
Internet builders who create ASP.NET net apps kind the biggest group of builders on the planet after the builders who construct PHP-based purposes. And with regards to constructing high-traffic-based web sites, ASP.NET wins the race. In response to a survey report by W3Techs, ASP.NET is the second hottest programming language to be adopted after JAVA for net purposes with greater site visitors charges.
Having said that, when an online software is liable to extreme site visitors, superior safety measures have to be adopted to make sure its safety. Allow us to look into the various kinds of safety greatest practices that may be adopted to keep away from vulnerabilities in an online software.
1. Cross-Web site Scripting (XSS)
It’s a kind of net software safety vulnerability that enables attackers to inject client-side scripts or malicious code into net pages that different customers see. It differs from different net assaults, reminiscent of SQL injection, which don’t immediately goal net purposes. Script injection could be carried out via Type Inputs, URL Question Strings, and HTTP Headers.
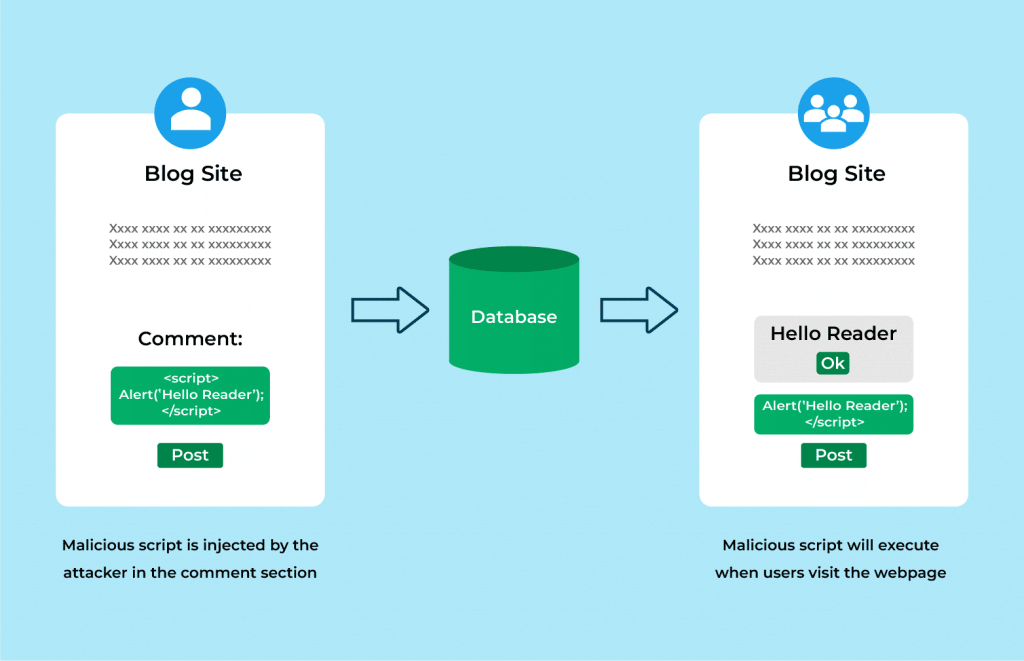
Sorts of Cross-Web site Scripting (XSS) assaults
Mirrored XSS, DOM-based XSS, and Saved XSS are the three principal forms of XSS vulnerabilities. The most typical kind of XSS vulnerability is mirrored XSS. An attacker can inject payloads (also referred to as metadata) into the sufferer’s request in order that the payload script is included within the request and mirrored within the HTTP response.
Doc Object Mannequin (DOM) Based mostly XSS is a extra superior kind of XSS assault that happens when a consumer script builds DOM utilizing information equipped by the consumer. In saved XSS, the attacker injects a script that’s persistently stored within the sufferer software. For instance, a malicious script could be injected into any enter kind on a web site, reminiscent of a remark space, and the sufferer will see this web page otherwise.
Prevention of Cross-Web site Scripting (XSS) assaults
Common Expression
Common expressions can be utilized to validate the consumer’s kind inputs. So, earlier than permitting the consumer to maneuver additional, one can block the dangerous letters and symbols and permit solely the required characters within the enter space. So, such validation (consumer and server-side each) can stop the malicious information from harming the web site.
Encoding the HTML
HTML encoding may help keep away from XSS assaults on web sites that settle for HTML markup as enter. It entails encoding the HTML that’s saved. The Razor engine routinely encodes all inputs. Subsequently the script part that will get inserted as any area isn’t run. Moreover, you may also apply an encoding rule to the variable by utilizing the @ directive.
URL Encoding
Most often, plain textual content is utilized in URL question strings, which can be utilized to conduct cross-site scripting (XSS) assaults. Because of this, the question parameter enter within the URL needs to be encoded. With ASP.web core 2.0 and better variations, the UrlEncode and UrlDecode strategies of Microsoft.AspNetCore.WebUtilities class can be utilized to encode and decode URLs.
2. SQL Injection
It’s the most prevalent assault, by which malicious SQL code is injected into the database and data is obtained by an unauthorized consumer. For instance, via SQL injection, the consumer receives the knowledge that they don’t have the authority to see. On this assault, a hacker continuously makes an attempt to insert SQL statements into the database, inflicting it to run and retrieve untested information.
Prevention of SQL Injection
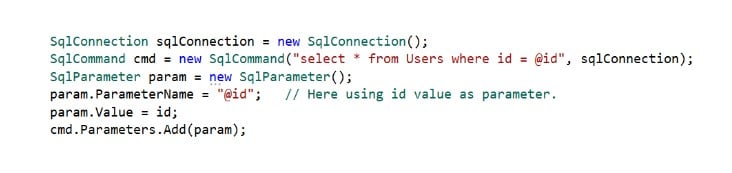
Parameterized Question
As an alternative of utilizing an inline question, one ought to use a saved process. To guard the appliance from SQL Injection, one should use a parameterized question when utilizing an inline question. The next is an instance of a parameterized question.
ORM reminiscent of Entity Framework
Utilization of ORM or Object-relational mapping maps SQL objects like desk view to the area objects like class. The ORM generates a parameterized question internally to get a file from the database.
Restricted Permissions for DB Entry
For tables with confidential information, one ought to restrict the DB consumer permissions. Tables linked to funds and transactions, for instance, ought to have their insert, replace, and delete rights restricted, as ought to tables that retailer a consumer’s private data. If a consumer completely works with choose queries, then he ought to solely give permission for the Choose assertion and never the Insert, Replace, or Delete statements.
Knowledge Encryption
It’s advisable to not retailer confidential data reminiscent of e mail addresses and passwords in a database in plain textual content. It needs to be stored encrypted always.
3. Cross-Web site Request Forgery (CSRF)
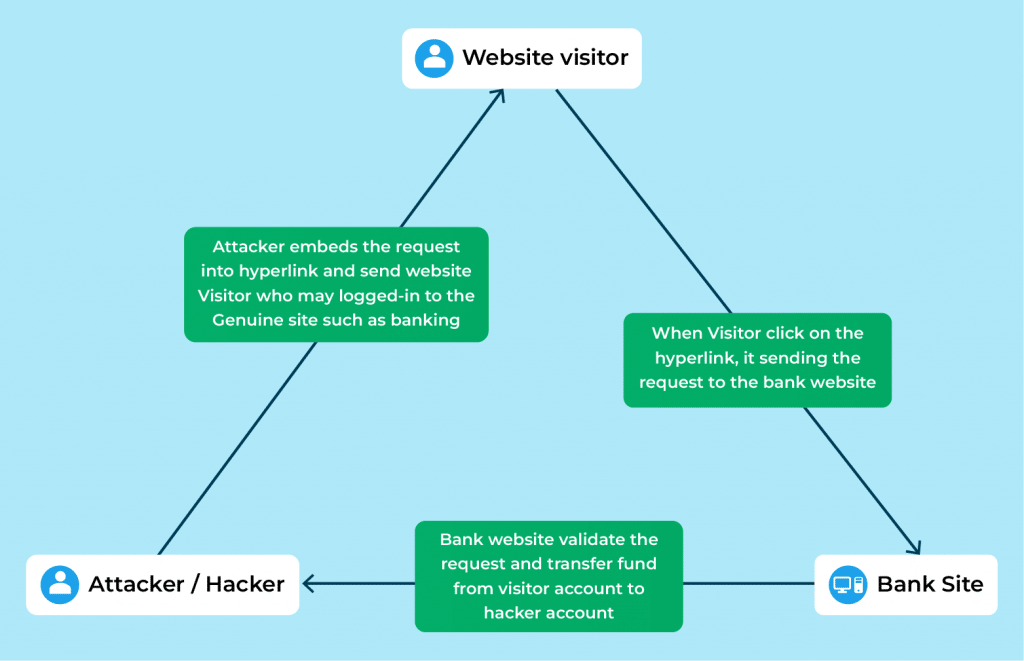
One other identify for it’s session driving. Utilizing this technique of assault, the attacker copies forging as a dependable supply and delivers the information to the web site. The web site processes this information, assuming it originated from a reliable supply. This type of assault can destroy consumer relationships in addition to what you are promoting. Unauthorized monetary transfers, information theft, and different types of CSRF are situations.
Usually, that is carried out by making a cast web site that communicates with the professional web site internally after which does malicious actions whereas the consumer session remains to be energetic. For instance, a consumer transfers funds from one account to a different, and the consumer and the financial institution website have established a safe connection. On the similar time, the consumer clicks on probably dangerous hyperlinks in junk e mail (that despatched by the attacker). The attacker takes benefit of the safe session between the consumer and the financial institution website and executes malicious operations reminiscent of monetary transfers. Nevertheless, this can be a server (net software) vulnerability relatively than an end-user challenge.
Prevention of Cross-Web site Request Forgery (CSRF)
You possibly can keep away from this sort of assault by utilizing AntiForgeryToken.
The HTML tag helper asp anti-forgery could be set to true in an HTML attribute. By default, this worth is fake. An anti-forgery token might be generated if this worth is about to true. The [ValidateAntiForgeryToken] factor have to be added to the shape publish motion technique to confirm {that a} professional token is generated.
4. Correct Error Dealing with
It may very well be a risk that an internet software’s error-handling code is miswritten.
Because of this, customers could also be uncovered to delicate data reminiscent of database setup data, desk names, saved procedures, information buildings, and programming coding buildings. An attacker/hacker may use this data to plan an assault on the web site.
Prevention
You possibly can keep away from such a scenario by establishing a customized error web page that seems when an error happens or by writing the code to deal with customized errors. Within the first answer, one should develop a web page with a generic message that have to be configured utilizing the startup class’s Configure technique.
One may use customized code to deal with exceptions, reminiscent of a try-catch block, an exception handler, or an exception filter.
5. Imposing SSL (Safe Sockets Layer) and utilizing HSTS
SSL establishes a safe connection between an online server and a browser. It ensures that every one information despatched between the net server (software) and the browser is encrypted and doesn’t alter throughout the switch. One can make the most of HTTPS (HyperText Switch Protocol Safe) to safe the net software. Adopting HTTPS has quite a few benefits, together with confidence, validated information, information integrity, and so on.
One can assemble an online software configured over HTTPS utilizing ASP.web Core 2.1 and subsequent variations. Earlier than the.NET core framework 1.1, one may configure HTTPS with ASP.web Core, however it was a bit extra complicated. When one creates an online software with Visible Studio, he has the choice of configuring the net software over HTTPS. HTTPS is enabled for the appliance within the template of an online software.
HSTS (HTTP Strict Transport Safety Protocol) is an online software safety technique that guards in opposition to downgrade protocol assaults and cookie hijacking. It makes the net server use an HTTPS connection to speak. Insecure connections are at all times rejected. The HSTS middleware is included by default within the Asp.web core template. It’s not advisable to make use of in a growth surroundings as a result of the browser caches the HSTS header.
One can override the next choices when configuring HSTS
MaxAge: A interval that defines the Strict-Transport-maximum Safety’s age. 30 days is the default worth.
IncludeSubDomains: The Strict-Transport-Safety header might be out there for subdomains if this worth is about to true.
Preload: The Strict-Transport-Safety module now helps preload.
Excluded Hosts: A listing of host names for which the HSTS header won’t be added.
One other middleware is included within the default template, redirecting requests from non-secure HTTP to safe HTTP. The request is redirected utilizing the default redirect standing code (307). Chances are you’ll customise this middleware to fulfill your wants. You possibly can override the default setting by including the AddHttpsRedirection technique to the starter class’s ConfigureService technique. Additionally, you’ll be able to set the default redirect standing code and the HTTPS port right here.
6. XXE (XML Exterior Entities) assault
An XXE (XML Exterior Entity) assault is conceivable on this system that parses XML enter. This assault may very well be as a result of the XML enter comprises a reference to an exterior entity that was misconfigured within the XML parser. It may occur on account of the hacker scanning the port the place the appliance (XML parser) is hosted, the leak of confidential information, SSRF (server-side request forgery), denial of service (Dos), and so forth. By injecting entities into entities, a hacker or attacker can use XML to trigger a Denial of Service assault. The “Billion Laughs Assault” is this sort of assault. Because of this, the system required extra sources to perform the duty, and the server could have crashed owing to extreme utilization.
Prevention of the Assault
To parse XML recordsdata with XmlTextReader, one should set the DtdProcessing attribute to Prohibit or Ignore.
Whether it is set to Prohibit, an exception might be thrown if a DTD (Doc Kind Definition) is discovered.
If it’s set to Ignore, all DTD specs within the doc might be disregarded, and the doc will proceed to be processed.
It should parse any DTD necessities within the doc if one units it to Parse. By default, DtdProcessing is about to Parse. It has the potential to be inclined.
7. Improper Authentication and Session Administration
The authentication module is current in most net purposes, and we needs to be cautious when constructing code. One could make errors reminiscent of failing to take away authentication cookies after profitable logout. Because of this error, attackers might be able to steal consumer credentials reminiscent of cookies and session settings, permitting them to entry the whole program and trigger important hurt.
The next errors can help information theft by attackers:
The connection isn’t safe (with out SSL).
Predictable login credentials.
Maintaining uncooked (non-encrypted) credentials on the server.
Logging out of purposes incorrectly.
Prevention
- After you’ve efficiently logged out, delete your cookies.
- SSL is used to guard cookies and periods.
- Set HTTP solely to safe cookies.
8. Model Disclosure
The request and response objects comprise varied information, together with the request technique, distant deal with, and server X-Powered-By, amongst different issues. A few of them, reminiscent of X-Powered-By and Server, are extraordinarily delicate. They have to not reveal this data to the end-user for the reason that attacker could use it to launch an assault. It’s possible that some framework variations will embrace safety flaws and that an attacker will use them to interrupt the system.
One can get data reminiscent of a server, X-Powered-By, and X-sourcefiles from the Header. The Server property signifies which server is used to host the appliance, the X-Powered-By signifies the details about the framework, and X-Supply Recordsdata is simply out there in debugging modules in IIS / IIS categorical.
Answer
The answer is to take away headers that comprise delicate data. One can take away the server header by organising AddServerHeader to false the place we configure the server. We are able to take away the X-Powered-By header both by utilizing net.config or from the IIS setting.
Conclusion
The above article has been put collectively to spotlight the perfect practices for securing ASP.NET Core MVC net purposes.
Keep up to date on the newest innovation and all the things tech- from rising applied sciences to previous transformations with Capital Numbers. We’re a full-service offshore net growth firm providing devoted sources throughout the globe
Feedback