Utility Programming Interfaces (APIs) have turn out to be the spine of recent software program improvement in right this moment’s linked digital surroundings. They permit for the seamless interchange of knowledge and performance between techniques, selling innovation and bettering person experiences. Amazon Net Companies (AWS) has developed as a key platform for internet hosting and administering APIs, offering a strong and scalable surroundings for designing and deploying APIs for the reason that daybreak of cloud computing. Nonetheless, better connectivity comes with elevated safety vulnerabilities, making API safety a high precedence for software program options firms.
Introduction to API Safety
API safety is essential in API improvement to construct and keep safe and dependable functions. It prevents unauthorized entry, information breaches, and different safety risks to your Utility Programming Interfaces. As a result of APIs continuously hyperlinks between totally different software program elements, defending them is essential for avoiding vulnerabilities that may disclose delicate information or interrupt operations.
The Significance of API Safety
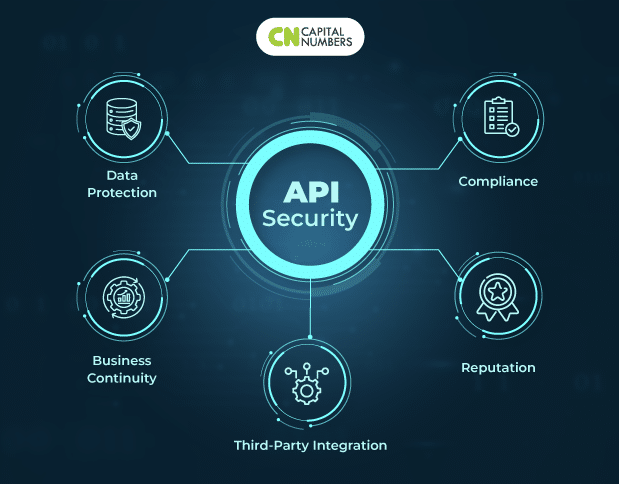
• Knowledge Safety: Safeguarding delicate information is on the coronary heart of the difficulty. APIs are used to speak a variety of delicate data, together with person passwords, private information, monetary information, and extra. On this setting, a safety breach would possibly sign catastrophe, with unthinkable penalties resembling information theft, id fraud, monetary losses, and everlasting reputational hurt. Thus, information safety is not a luxurious within the digital period however an essential want.
• Enterprise Continuity: Except for information safety, the integrity of APIs instantly impacts enterprise continuity. Unsecured APIs are an open invitation to hostile actors that want to disrupt techniques or trigger systemic breakdowns. Such interruptions could also be disastrous, leading to prolonged downtimes, income losses, and, consequently, a lack of confidence amongst clients, companions, and stakeholders.
• Compliance: Adherence to regulatory compliance is required in an period of accelerating emphasis on information privateness and safety. The Common Knowledge Safety Regulation (GDPR) and the Well being Insurance coverage Portability and Accountability Act (HIPAA) are two examples of strict legal guidelines that a number of companies and geographical places have enacted. These requirements require stringent information safety practices and levy harsh fines for noncompliance. Because of this, inadequate API safety jeopardizes information and exposes organizations to vital authorized and monetary implications.
• Fame: API safety is crucial for model picture upkeep within the digital surroundings, the place fame and belief are useful property. A safety breach could irreversibly hurt a model’s fame and destroy buyer confidence. Rebuilding broken belief is usually a mammoth job with long-term ramifications.
• Third-Celebration Integration: APIs are not often utilized in isolation. They usually interface with techniques and companies supplied by third events. The safety of your APIs instantly impacts the safety posture of those linked techniques. An unsecured API could cause a series response, leading to vulnerabilities and potential breaches all through a linked community of digital processes.
API Safety Finest Practices
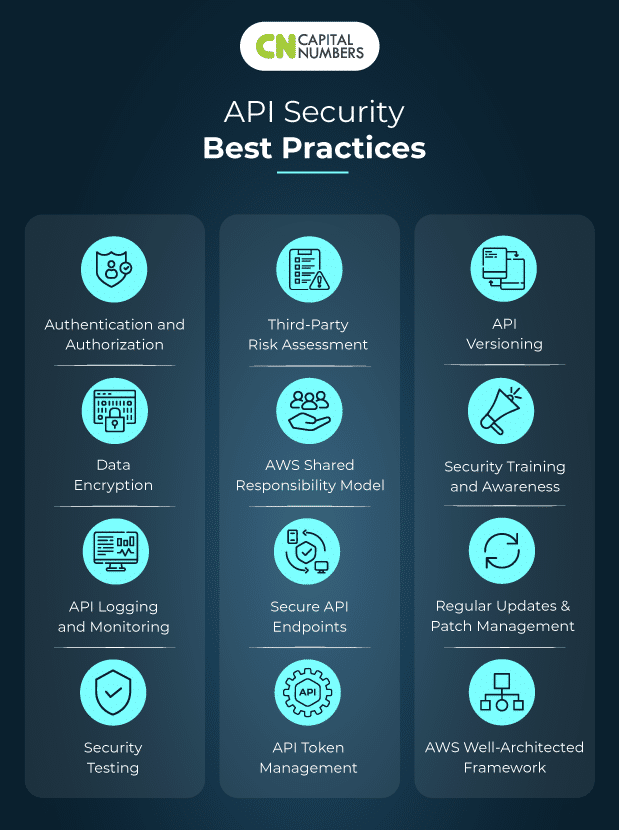
AWS consultants give attention to API safety to forestall information breaches, guarantee compliance, safeguard AWS sources towards unauthorized entry, and extra. Following are the total API safety finest practices really useful by Capital Numbers, with an emphasis on AWS:
1. Authentication and Authorization
- Authentication verifies the id of customers or techniques making an attempt to entry the API, whereas authorization determines the extent of entry granted to authenticated entities.
- Make use of industry-standard authentication strategies like OAuth2, JWT (JSON Net Tokens), or API keys.
- Leverage AWS Identification and Entry Administration (IAM) to handle entry to AWS sources securely. Be sure that IAM insurance policies are well-defined and restricted to the minimal required permissions.
- Assign particular roles and permissions to customers or techniques to make sure they will solely entry approved sources.
2. Safe API Endpoints
- API endpoints are the entry factors to your system. Securing them is a basic step in API safety.
- Validate and sanitize person enter to forestall widespread vulnerabilities like SQL injection and Cross-Web site Scripting (XSS).
- Amazon API Gateway is a crucial element for managing and securing APIs. Configure it to deal with authentication, request validation, and charge limiting.
- Make the most of AWS API Gateway’s request validation options to outline and implement enter validation guidelines, guaranteeing that solely well-formed, secure requests attain your backend.
- Implement charge limiting utilizing AWS API Gateway’s built-in options to forestall abuse and brute-force assaults.
3. Knowledge Encryption
- Encrypting information in transit and at relaxation protects delicate data from interception or theft.
- Use HTTPS to encrypt information in transit and be sure that your SSL/TLS certificates are up-to-date.
- Use AWS Certificates Supervisor (ACM) to handle SSL/TLS certificates to your AWS APIs.
- Make use of encryption mechanisms to guard information at relaxation or saved in databases or on disk. Make the most of AWS companies like Amazon S3, Amazon RDS, or AWS Key Administration Service (KMS) to encrypt information at relaxation.
- Use AWS Key Administration Service (KMS) to handle encryption keys and outline fine-grained entry controls for information encryption.
4. API Token Administration
- Managing API tokens, resembling API keys or entry tokens, is essential to stopping unauthorized entry.
- Repeatedly rotate API tokens to restrict publicity within the occasion of compromise. Leverage Amazon API Gateway API keys for authentication and limit entry primarily based on API keys.
- Use AWS API Gateway API keys to manage entry to your APIs and arrange utilization plans to handle charge limits and quotas.
5. API Logging and Monitoring
- Complete logging and real-time monitoring assist detect and reply to safety incidents.
- Preserve detailed logs of API actions to trace suspicious conduct. Allow AWS CloudTrail to seize API calls and monitor AWS useful resource modifications.
- Implement SIEM options to observe and analyze API logs for anomalies. Arrange Amazon CloudWatch alarms to set off notifications for suspicious actions.
- Create CloudWatch dashboards and alarms to realize insights into the efficiency and safety of your AWS APIs.
6. API Versioning
- Preserve backward compatibility whereas evolving your APIs to make sure current integrations stay safe.
- Use versioning schemes like Semantic Versioning (SemVer) to obviously talk modifications and guarantee easy upgrades.
7. Safety Testing
- Repeatedly check your APIs for vulnerabilities utilizing instruments like penetration testing and safety scanning.
- Conduct common penetration checks to determine weaknesses in your API safety. Make the most of AWS Inspector to evaluate the safety of your AWS sources and APIs.
- Make use of static and dynamic evaluation instruments to scan code for vulnerabilities. Think about using third-party vulnerability scanning instruments that combine seamlessly with AWS.
- Leverage AWS Inspector to automate safety evaluation duties, together with vulnerability scanning and compliance checks.
8. Safety Coaching and Consciousness
- Educate your improvement and operations groups about API safety finest practices.
- Present coaching on safe coding practices and customary safety threats. Make the most of AWS coaching sources and certifications to make sure your group is well-versed in AWS safety.
- Develop and usually replace an incident response plan to deal with safety breaches promptly. Create a selected incident response plan for AWS to deal with safety incidents throughout the AWS Cloud.
9. Third-Celebration Threat Evaluation
- Assess the safety practices of third-party APIs your system interacts with.
- Consider the safety controls and practices of third-party API suppliers earlier than integration.
10. Common Updates and Patch Administration
- Maintain your API frameworks, libraries, and dependencies up-to-date to mitigate identified vulnerabilities.
- Monitor safety advisories and apply patches promptly to deal with identified vulnerabilities.
11. AWS Shared Accountability Mannequin
- Perceive the AWS Shared Accountability Mannequin, which defines the division of safety tasks between AWS and the shopper.
- Pay attention to your tasks for securing information and configurations inside AWS companies.
12. AWS Properly-Architected Framework
- Comply with the AWS Properly-Architected Framework’s safety finest practices to design and function safe and resilient workloads.
- Pay explicit consideration to the Safety Pillar of the AWS Properly-Architected Framework, which guides on implementing safety finest practices.
Additionally Learn : What Is Serverless Computing?
Conclusion
API safety throughout the AWS ecosystem is crucial to fashionable cloud computing. Capital Numbers, a reputable software program options firm, acknowledges the significance of safeguarding your information within the age of interconnected techniques and APIs hosted on AWS. By following these complete API safety finest practices particularly tailor-made for the AWS ecosystem, you may considerably cut back the chance of safety breaches, defend your information, and keep the belief of your clients and companions. Keep in mind that API safety shouldn’t be a one-time effort however an ongoing dedication to remain forward of evolving digital and cloud computing threats. Keep vigilant, knowledgeable, and proactive in securing your APIs within the AWS cloud.
Feedback