That is half three of a three-part collection on product infrastructure safety.
The assault vectors within the cloud are continually evolving. These assaults regularly use unpatched vulnerabilities and insecure configurations to realize entry to your techniques. Fast and efficient detection and proactive remediation is the important thing. As a startup constructing your small business within the cloud, changing into the goal of a malicious assault can set you again out of your friends. Microsoft Defender for Cloud has in-built controls and built-in instruments that may defend you from such predicaments.
On this weblog collection, we began off by discussing the relevance of safety posture administration and the right way to get began with the service. Within the second half, we seemed on the steps to get began with a number of the key options of Microsoft Defender for Cloud that can provide help to get began with the service. Within the concluding a part of this collection, we’ll deep dive additional into the capabilities of Microsoft Defender for Cloud that can assist defend your surroundings from malicious assaults.
Assess safety posture by way of safe rating
For startups working in extremely regulated trade verticals, making certain compliance can contain in depth efforts. The choice to obtain a certificates demonstrating how safe your infrastructure and companies are will assist make this course of go extra easily. The safe rating supplied by Microsoft Defender for Cloud primarily based on main compliance requirements places forth the best answer for this.
What’s Microsoft Safe Rating?
The safety standing of your deployments is constantly assessed by Microsoft Defender for Cloud and the outcomes are quantified as a safe rating. The safe rating is displayed as a share, and the service additionally shows the safety findings that contribute to the rating.
The Safe rating might be seen from Microsoft Defender for Cloud > Safety posture. The safety posture of various related environments will also be seen from right here:
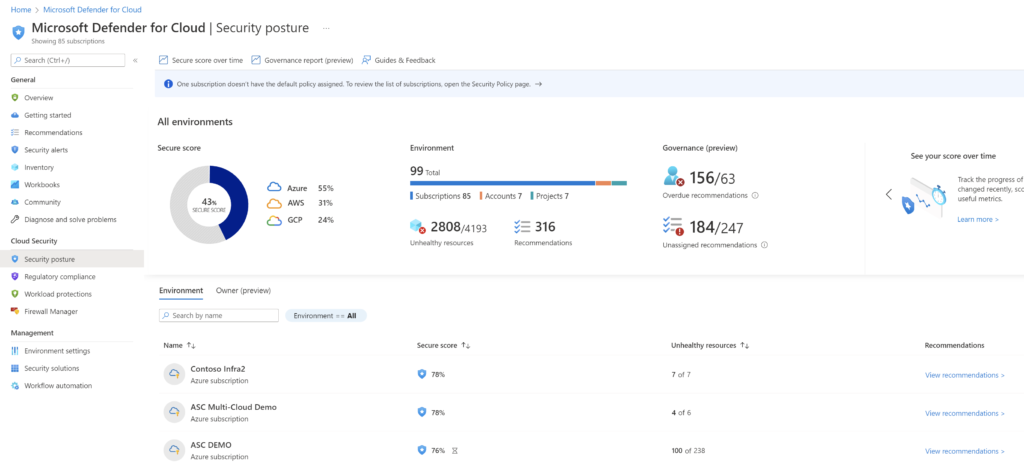
Click on on Suggestions to see the controls and proposals for every surroundings. The view additionally reveals the utmost rating for every management, the present rating and potential rating improve that’s attainable by remediating the findings.
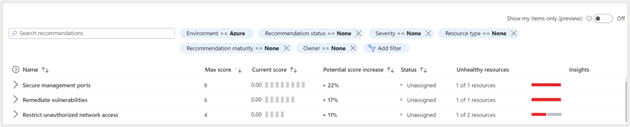
You’ll be able to broaden the safety management to see the suggestions related to it. For instance, proven beneath are the suggestions related to the management “Safe administration ports.” This management gives steerage on securing the administration ports related together with your assets. If left unprotected, these ports might be focused by brute pressure assaults to realize entry to the surroundings.
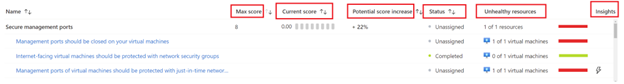
Max rating: If all findings are remediated, the utmost attainable rating will likely be 8. The rating is related to a management primarily based on its relevance to the respective surroundings. The suggestions related to the management having the best rating must be prioritized first.
Present Rating: It reveals the present rating primarily based on the variety of assets which can be already in step with the suggestions.
Potential rating improve: This part reveals the proportion by which the rating might be elevated by remediating the suggestions.
Insights: It provides you further details about the respective suggestions. The steerage supplied can be utilized to repair the findings. You may also arrange insurance policies that can both rectify the issue if somebody creates a non-compliant useful resource or altogether forestall the creation of assets with this subject.
Safe rating calculation: The rating related to a single safety management is calculated utilizing the next formulation
![]()
The rating related to every management rolls ups to supply the safe rating of the Azure subscription or different related cloud surroundings utilizing the beneath formulation:
![]()
When there are a number of subscriptions or related AWS/GCP environments the general safety posture is calculated utilizing the next formulation
![]()
Observe that Microsoft Defender for Cloud assigns a weight to every surroundings relying on parameters such because the variety of assets in that surroundings.
Resolve threats and enhance safe rating
Microsoft Defender for Cloud protects your subscriptions by implementing safety initiatives. A number of safety insurance policies are included in these initiatives. Every of those insurance policies yields a safety suggestion for strengthening your posture.
Safety coverage: Azure insurance policies assist implement subscription extensive restrictions like utilization of tags, naming conference, allowed areas. A safety Coverage makes use of the identical constructs to create a algorithm for controlling sure safety configurations. Defender for Cloud insurance policies can both be “Audit” or “Implement” insurance policies. ‘Audit’ insurance policies, examine and report on sure safety configurations. “Implement” insurance policies then again that can be utilized to implement safe settings.
Safety initiative: A Microsoft Defender for Cloud safety coverage initiative is created in Azure coverage and is a group of safety insurance policies teams for a selected function. Azure Safety Benchmark is the default initiative assigned by Microsoft Defender for Cloud for all subscriptions. It’s constructed primarily based on trade customary controls derived from Nationwide Institute of Requirements and Know-how (NIST) and Heart for Web Safety (CIS). Along with this, you too can create initiatives primarily based on trade compliance requirements.
Safety suggestion: Relying on the safety initiative and the insurance policies included in it, Microsoft Defender for Cloud constantly analyzes your goal surroundings and gives safety suggestions.
Assessment suggestions
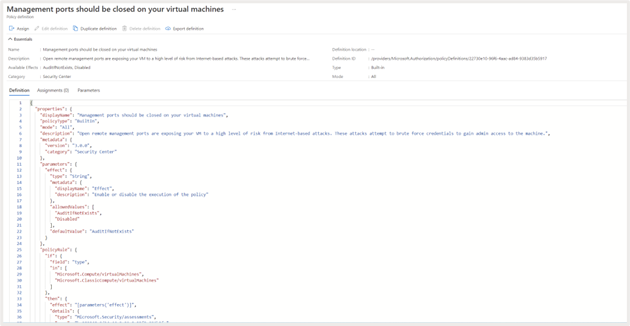
Let’s take a better have a look at one of many safety suggestions, “Administration ports must be closed in your digital machines.”
If you happen to click on on the advice, you’ll be able to see further data, together with. severity, description of the advice, remediation steps, affected assets, and many others.
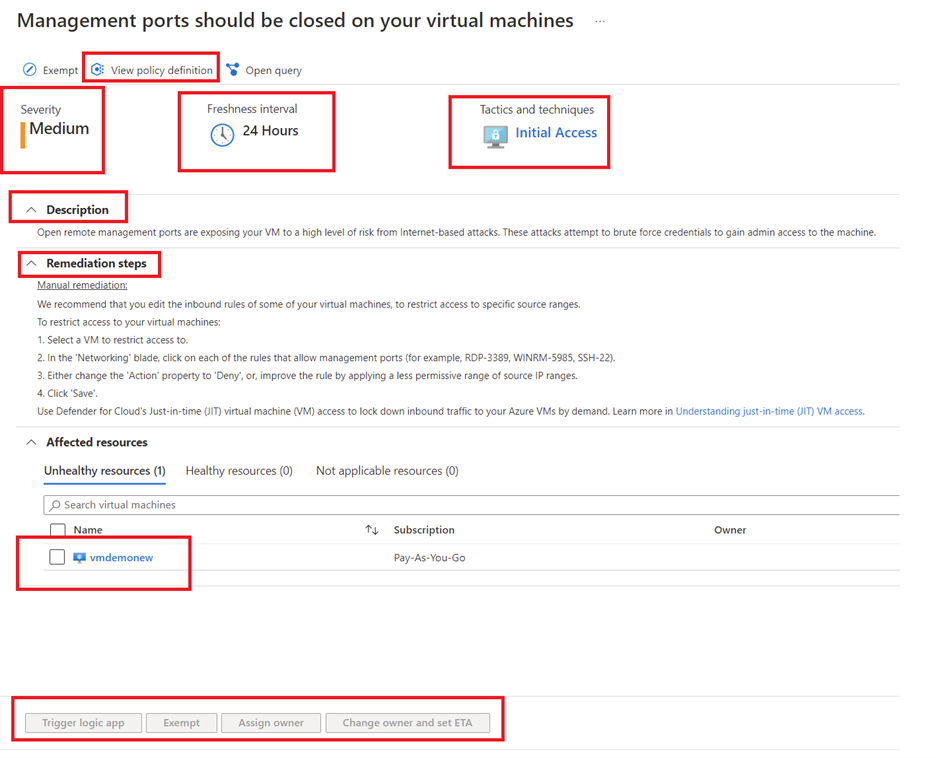
View coverage definition
You’ll be able to click on on “View coverage definition” to see particulars of the coverage related to the advice.
Severity
This defines the severity of the advice, that helps with prioritization of the advice.
Freshness
Offers insights on when the advice was issued.
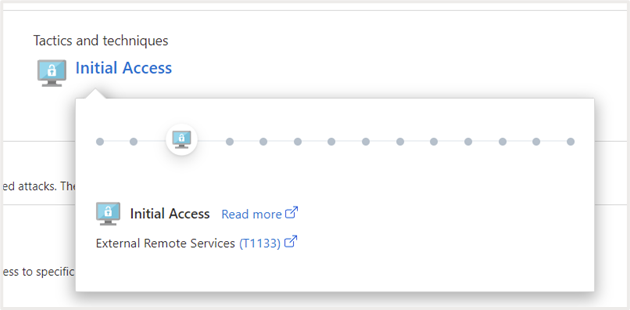
Ways and Strategies
This gives further data on MITRE ATT&CK techniques and strategies associated to the advice. You’ll be able to click on on the hyperlink to get further data.
Description
Explains why the management is vital and the way it may be exploited to assault your surroundings.
Remediation steps
Offers step-by-step steerage on the right way to implement the advice. For instance, the remediation steps on this case are as follows:
Handbook remediation
We suggest that you just edit the inbound guidelines of a few of your digital machines, to limit entry to particular supply ranges.
To limit entry to your digital machines:
- Choose a VM to limit entry to.
- Within the ‘Networking’ blade, click on on every of the principles that enable administration ports (for instance, RDP-3389, WINRM-5985, SSH-22).
- Both change the ‘Motion’ property to ‘Deny’ or enhance the rule by making use of a much less permissive vary of supply IP ranges.
- Click on ‘Save’.
Use Microsoft Defender for Cloud’s Simply-in-time (JIT) digital machine (VM) entry to lock down inbound visitors to your Azure VMs by demand. Be taught extra in Understanding just-in-time (JIT) VM entry.
Affected assets
Right here the assets for which the advice is relevant are listed. They’re segregated as follows:
- Unhealthy assets: Exhibits the assets the place the difficulty must be remediated
- Wholesome assets: Exhibits assets the place the difficulty is already remediated or these not impacted by the difficulty
- Not-applicable assets: Some assets can’t be evaluated in opposition to the advice and are marked as “not relevant assets”. This could possibly be due to corrupted VM extensions, lack of scanner, and many others. The rationale why the analysis isn’t performed may even be listed
Motion
You’ll be able to choose one of many affected assets and select to remediate the motion by Triggering a logic app or assign the proprietor to take motion . You may also select to Exempt the useful resource from this suggestion by deciding on the “ Exempt” possibility wherever relevant to align with organizational safety requirements.
Repair suggestions
Microsoft Defender for Cloud can repair a number of the suggestions straight from the console. Let’s discover how to do this for the advice “Machines ought to have a vulnerability evaluation answer.”
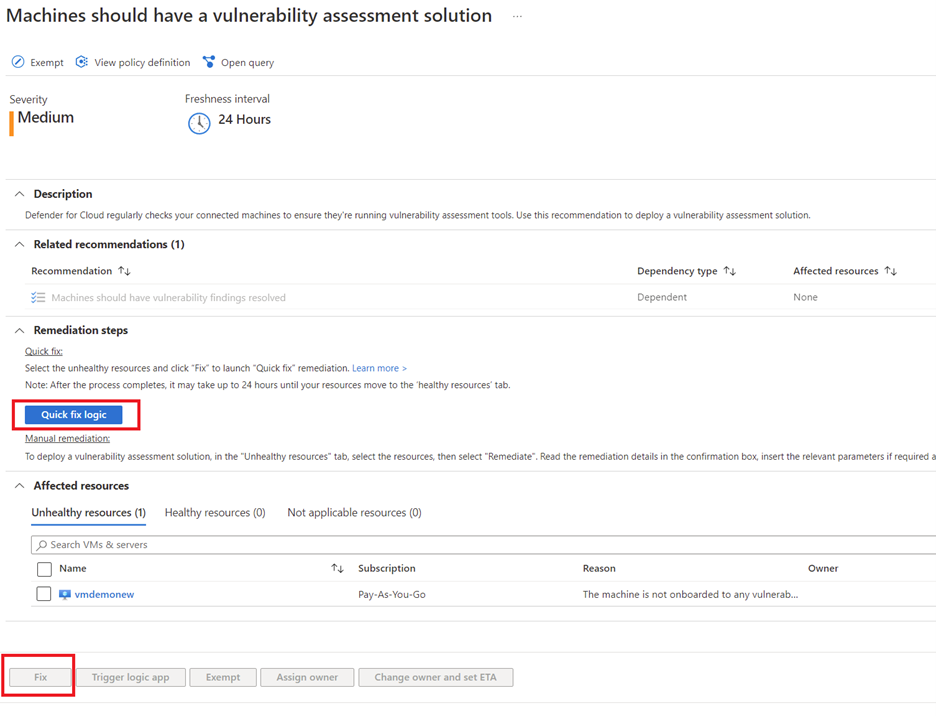
Fast repair logic
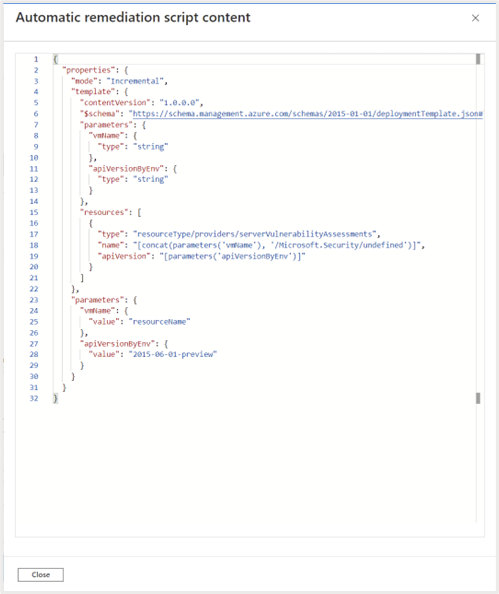
You’ll be able to click on on this hyperlink to view the remediation logic/script that will likely be used to repair the difficulty
To repair the difficulty choose the unhealthy useful resource and click on on “Repair”. That is provoke strategy of deploying vulnerability administration answer on the useful resource.
Learn how to examine useful resource well being
Microsoft Defender for Cloud gives a consolidated view of useful resource well being and proposals related to it. You need to have Useful resource Group contributor to view this, browse to Microsoft Defender for Cloud > Stock.
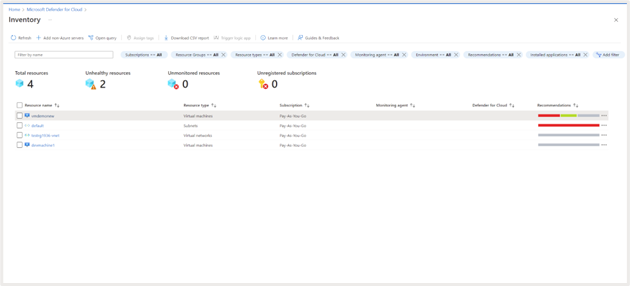
Click on on a selected useful resource to view the useful resource well being. You’ll get a view of suggestions, alerts and put in purposes for that useful resource.
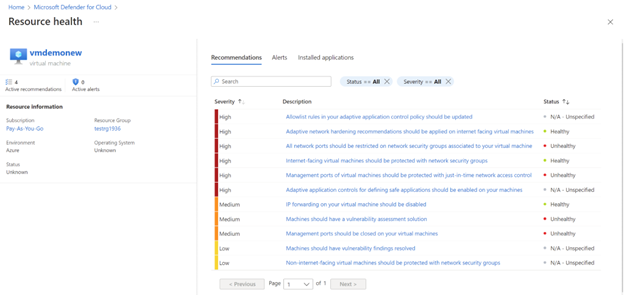
Click on any of the suggestions to take remedial motion.
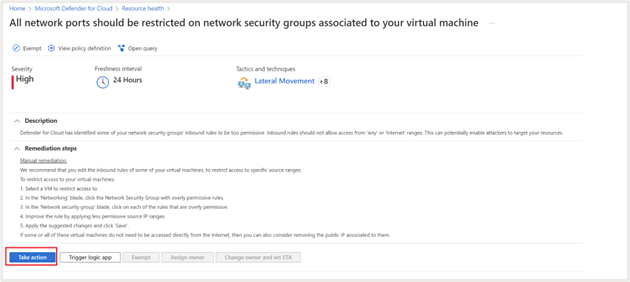
Click on on “Take Motion” or “Repair” (for some suggestions) to implement the remediation steps as mentioned within the earlier part
View and reply to safety alerts
Getting well timed safety alerts on detected assaults go a good distance in stopping catastrophic occasions. Microsoft Defender for cloud makes use of superior menace analytics and menace intelligence capabilities that may provide you with a warning about infiltration makes an attempt and malicious actions in your environments. You will get a unified view of safety threats detected in your surroundings, their severity and steerage on remediation steps upon getting Microsoft Defender for cloud enhanced safety features enabled.
To view detected safety alerts, browse to Microsoft Defender for Cloud > Safety alerts.
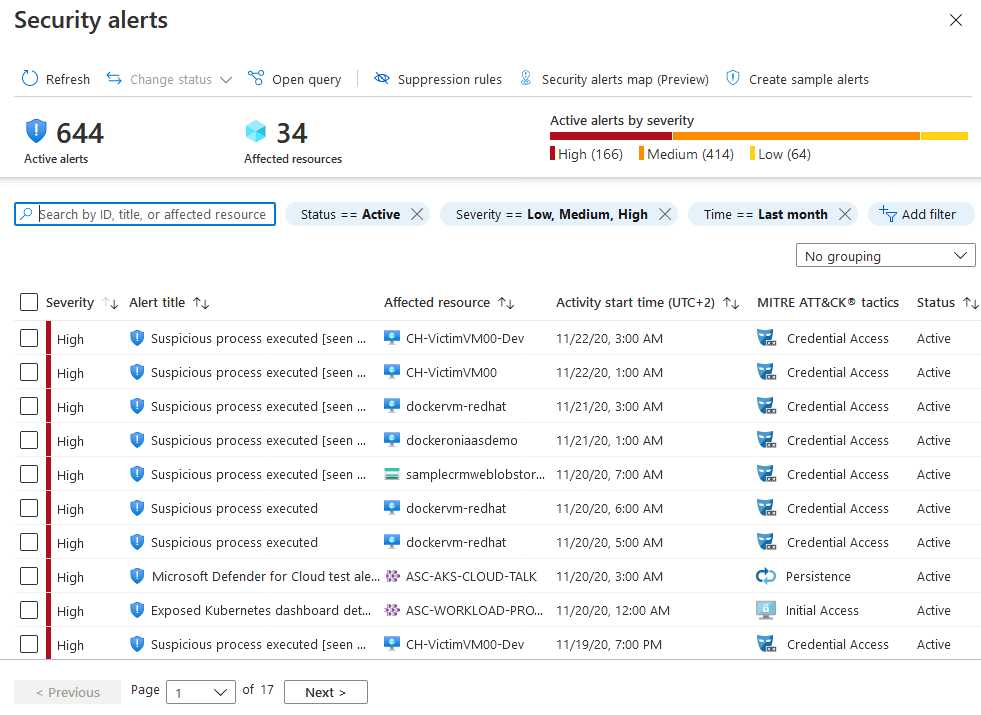
The alerts offered on this web page are categorized as excessive, medium, low, or informational, relying on Microsoft Defender for Cloud’s degree of confidence within the malicious intent behind the exercise that triggered the alert. It helps you prioritize and take motion on the alerts.
- Excessive: Signifies a excessive chance of the useful resource being compromised by an assault and must be instantly prioritized for remediation.
- Medium: Signifies a medium to excessive malicious intent detection, normally originating from anomaly-based detections or machine studying algorithms
- Low: These are low precedence occasions which will or might not be associated to an assault. Blocked assault makes an attempt are additionally displayed as Low severity if it must be seemed into
- Informational: These are occasions that aren’t malicious however must be investigated contextually to know whether it is associated to some other threats.
Let’s take a better have a look at one of many alerts and perceive how the remediation might be performed:
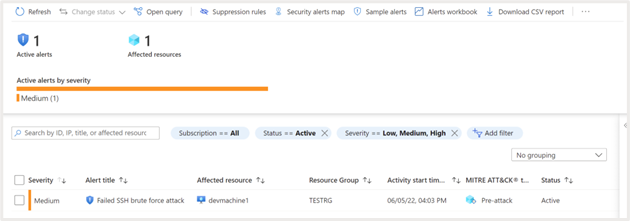
Click on on the alert to view further details about the assault:
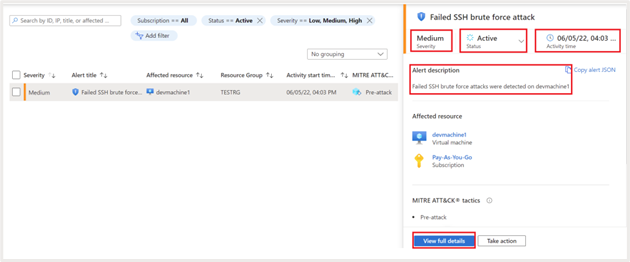
It reveals the next further particulars:
- Standing of the exercise. Detected alerts will likely be proven as “energetic” till essential motion is taken, and it’s marked as Dismissed manually
- Description. Give further details about the assault. On this case it’s a Failed SSH brute pressure assault
- Time at which the assault is detected
- Severity of the assault
- Kill chain intent evaluation primarily based on MITRE ATT&CK metric
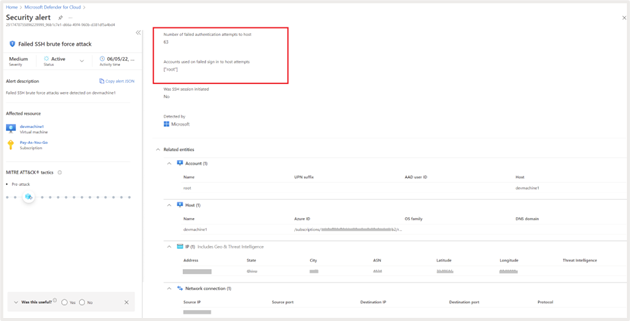
Click on on “View full particulars” for additional information. It provides granular data on the variety of instances the assault occurred; account used for the failed makes an attempt and many others. It additionally gives granular details about geo and menace intelligence, for instance, the geography, ASN, latitude, longitude, and many others., from which the assault originated.
Click on on “Subsequent: Take Motion” to view steerage on the remediation steps to be taken.
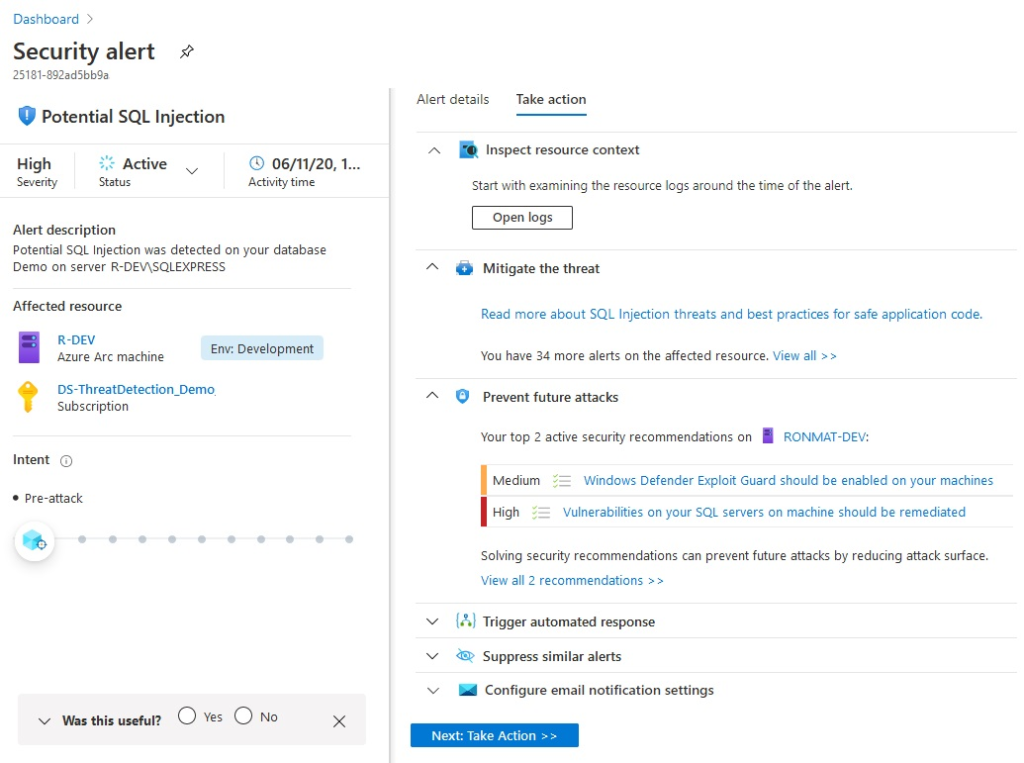
You’ll be able to view the logs generated across the time of occasions to determine correlated occasions by clicking on “Open logs.”
The steps to mitigate the menace are listed beneath the part “Mitigate the menace.”
Any hardening suggestions that may forestall such assaults sooner or later is listed beneath “Forestall Future assaults.”
If you wish to set off a logic app as response to the detection, it may be linked beneath “ Set off Automated response.”
If you happen to determine that the alert was a false optimistic you’ll be able to create a suppression rule from beneath the “Suppress related alerts” part.
You’ll be able to configure e-mail notifications to alert directors of this safety occasion from the “Configure e-mail notification settings.”
Abstract
Microsoft Defender for Cloud helps defend your multi-cloud and hybrid environments from current and rising threats. Utilizing superior menace detection capabilities, analytics and machine studying algorithms, Microsoft Defender for Cloud can present complete safety to your workloads.
On this three-part weblog collection, we explored all these subjects to offer you a head begin in your cloud safety posture administration journey. Startups with minimal funding in safety manpower can simply leverage the capabilities of Microsoft Defender for Cloud to safe your purposes no matter the cloud platform it’s hosted in. All the best way from quantifying the safety posture utilizing safe rating, offering actionable suggestions and alerts to intimate the suitable stakeholders, Microsoft Defender for Cloud has received you lined.
To get began with Microsoft for Startups Founders Hub, enroll at present.